…according to a Twitter post by the Chief Informational Security Officer of Grand Canyon Education.
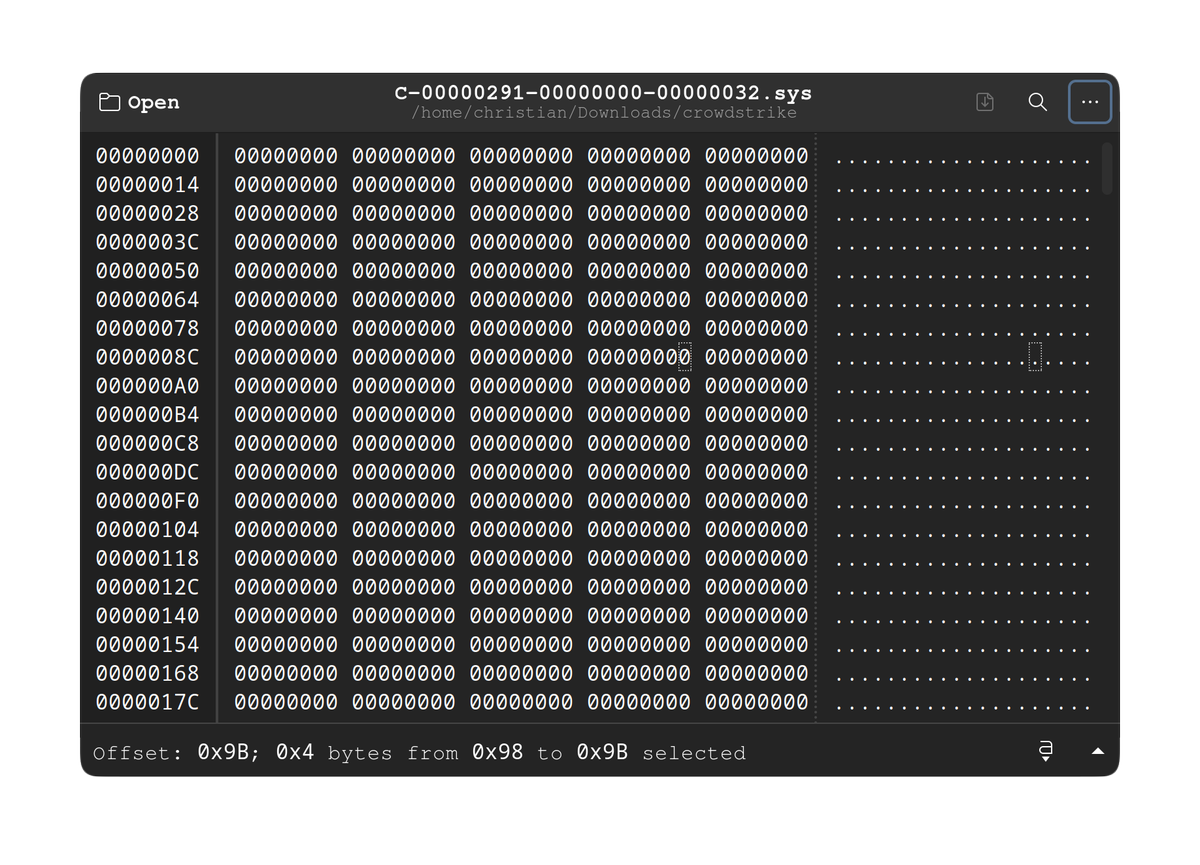
So, does anyone else find it odd that the file that caused everything CrowdStrike to freak out, C-00000291-
00000000-00000032.sys was 42KB of blank/null values, while the replacement file C-00000291-00000000-
00000.033.sys was 35KB and looked like a normal, if not obfuscated sys/.conf file?
Also, apparently CrowdStrike had at least 5 hours to work on the problem between the time it was discovered and the time it was fixed.


have they ruled out any possibility of a man in the middle attack by a foreign actor?
Or it being an intentional proof of concept
The CEO made a statement to the effect of “It’s not an attack, it’s just me and my company being shockingly incompetent.” He didn’t use exactly those words but that was the gist.
https://www.crowdstrike.com/blog/statement-on-falcon-content-update-for-windows-hosts/
I guess they could be lying, but if they were lying, I don’t know if their argument of “we’re incompetent” is instilling more trust in them.
“We are confident that only our engineers can fuck up so much, instead of our competitors”
In the middle of the download path of all the machines that got the update?
Foreign to who?
“Foreign” in this context just means “not Crowdstrike”, not like a foreign government.